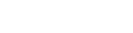Platform
Security platform for key information infrastructure
Demand Analysis
As China's Internet continuously develops at a high speed, the network and its devices are more intelligent, large-scale, and diversified. However, challenges on the aspect of security such as complex network space, variable network environment, and increased network risks appear as well, and they have become important factors affecting the healthy development of the economy and society.
Product Introduction
The Critical Information Infrastructure Security Protection (CII) is a set of overall solutions for public security organs to monitor network backbone nodes as well as important networking systems and websites within their jurisdiction. CII can monitor intrusion behaviors and virus transmission at network backbone nodes and Internet websites in real time, timely report on large-scale network intrusion behaviors, virus transmission and other events, as well as analyze and make early warning for the potential security risks and malicious attacks of the network.
Core Functions
The main functions include real-time monitoring, threat perception, reconnaissance and investigation, traceability, hierarchy protection, notification and warning, intelligence information, rapid disposal, command and dispatch, and offensive and defensive drills.
Product Advantages:
1. Three major-center designs provide visual presentation, deep mining analysis, basic scheduling and collection of data.
2. The super-fusion design, can be docked with the collection devices from other manufacturers, analyze intelligent data, and achieve multi-vendor data collision and association analysis.
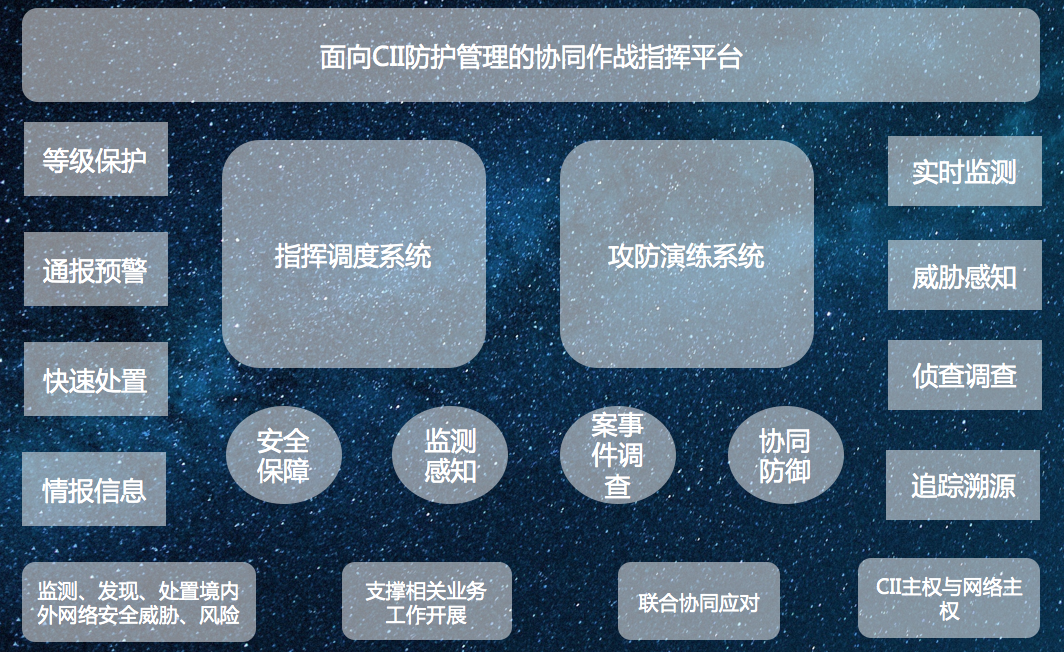
3. Intelligent analysis capability: The main functions include in-depth mining and validation of the results of the analytical model, analysis and mining of data through visual analysis or interactive analysis, and custom construction of new analytical models.
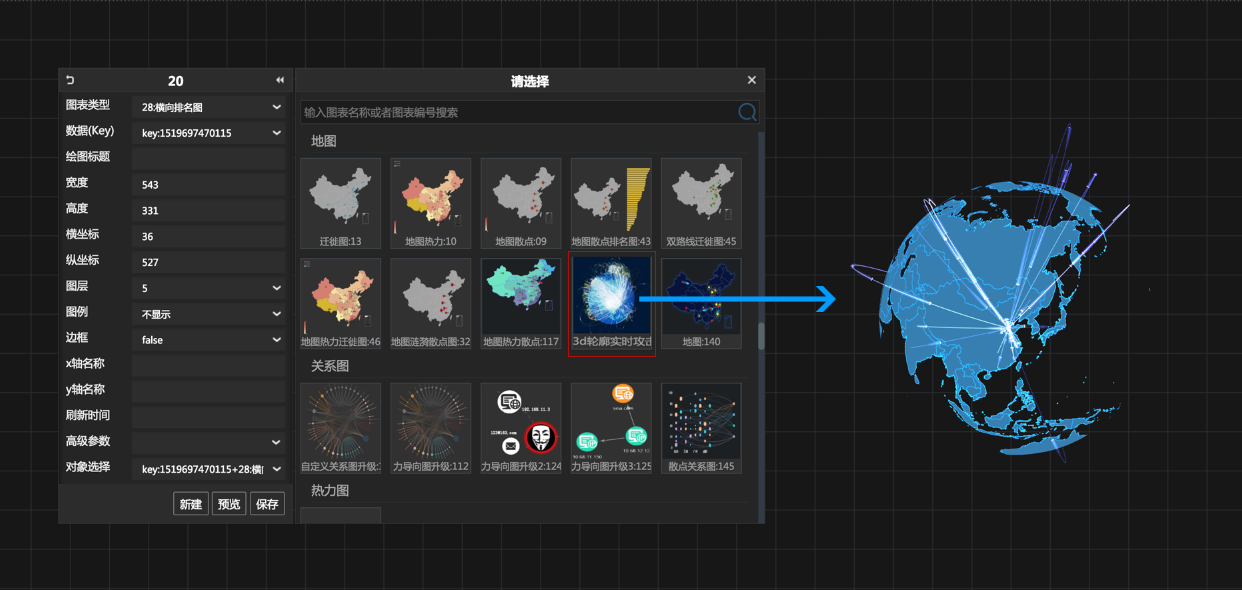
4. Threat intelligence capability: Possessing the intelligence information from multiple sources, gathering malicious IPs, malicious URLs, malicious programs, vulnerability information, etc. Facing the security threat of cyberspace, it uses the big data analysis and mining method to realize real-time threat monitoring for various industries and application systems.
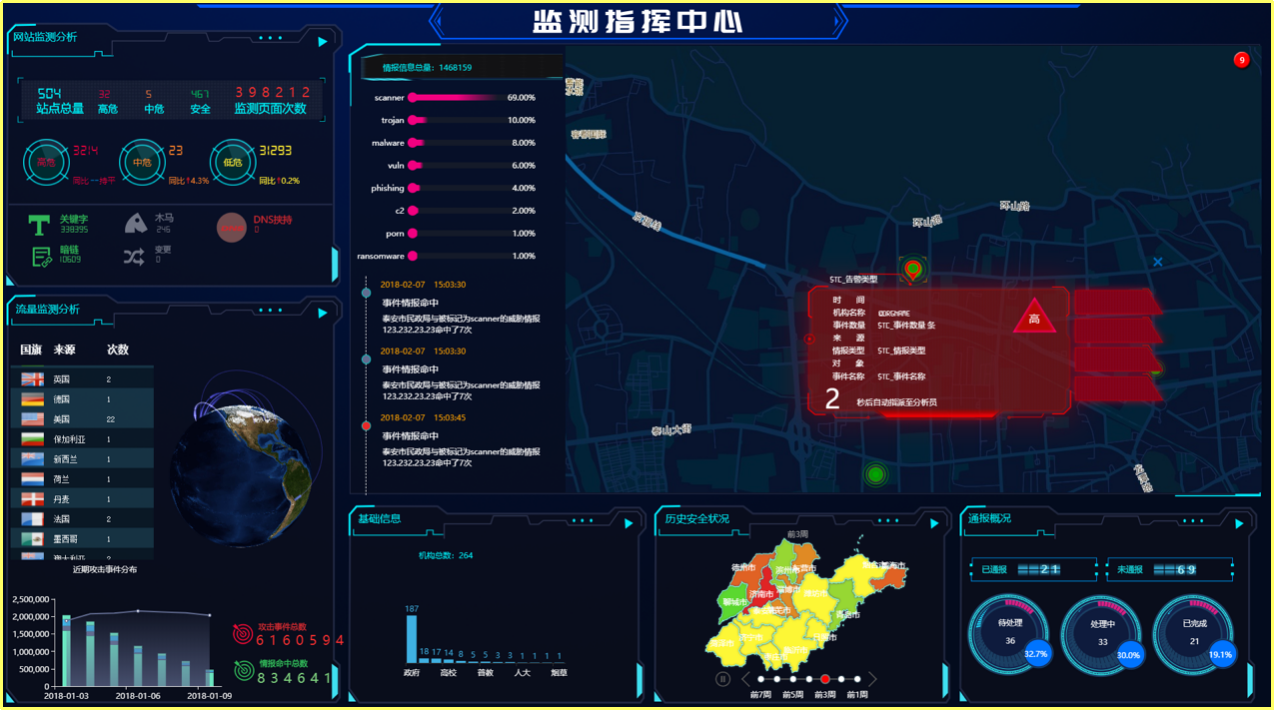
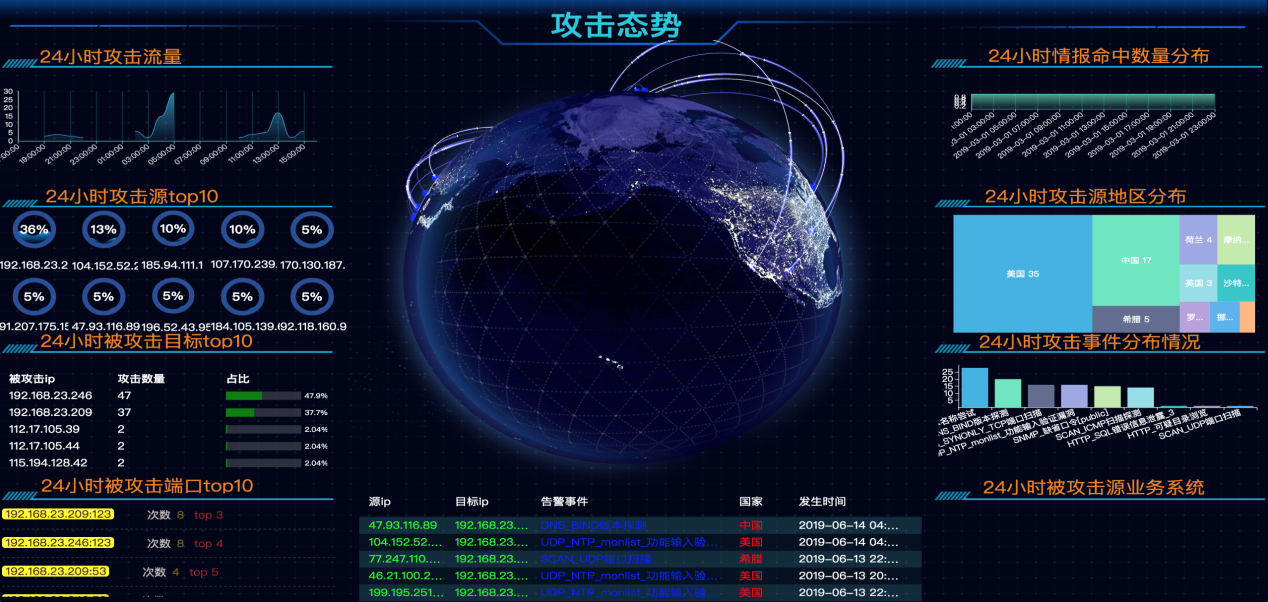
Typical application
Application scenarios

Deployment plan
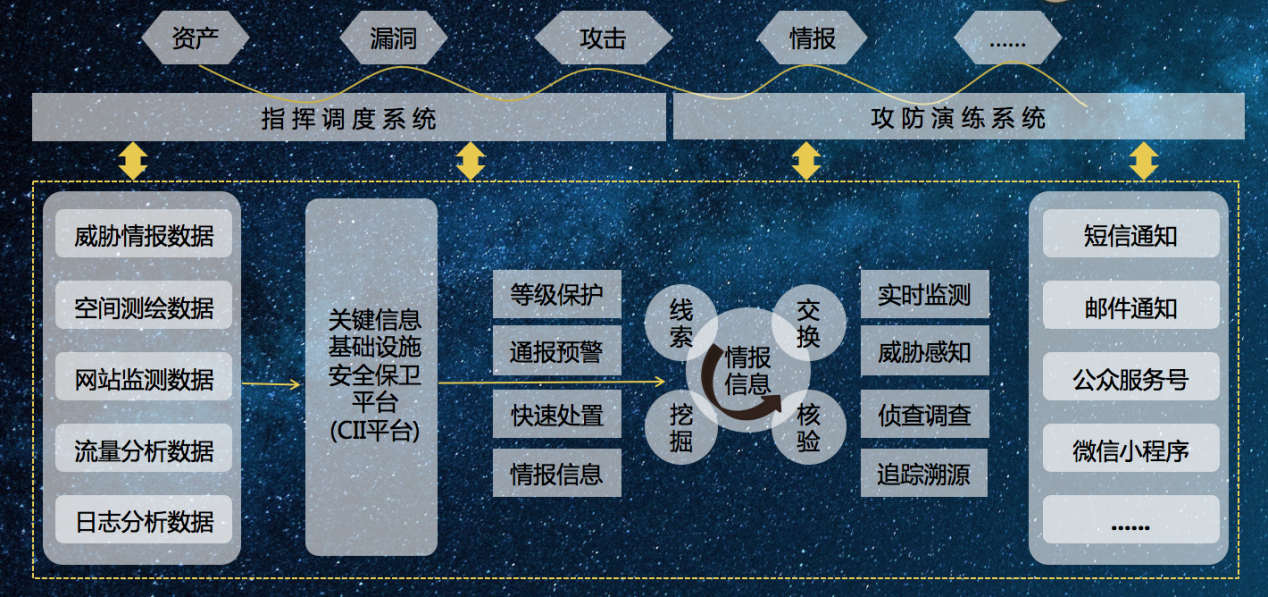
User value
Establishing a security threat data analysis and notification disposal center by collecting relevant data related to network security. Making an early warning on the network security threats in a certain period of time and in the future through network security event analysis based on big data. Conducting emergency response and disposal for relevant network security events through mechanism construction, to form the big data analysis capability for multi-source threat intelligence and the network security monitoring and early warning network covering the whole province, so as to build an information security notification system for internal and external linkages in the public security industry, and improve the capabilities of public security organs in terms of monitoring, discovery, situational awareness, early warning and emergency response.

Service hotline:
400-810-7766 (24H)
E-mail:
shfw@leadsec.com.cn
Address:
Zhongguancun, 8 dongbeiwang west road, haidian district, BeijingSoftware park 21