Platform
soc
LeadsecNetwork Security Management Platform (SOC)
Security Insight based on Data
Platform Introduction
The big data version of the Leadsec Security Management Platform (SOC) is a new generation of big data security management platform developed by Leadsec through the combination of many years of SOC experience and the mainstream big data on basis of traditional security management platform. It reconstructs the conventional security management platform using the big data processing technology, and is a set of measurable unified business support platform established from dimensions of monitoring, audit, risk as well as operation and maintenance, with IT assets as the basis, the business information system as the core, the security data as the drive and the customer experience as the guide, allowing various users to achieve monitoring on the availability and performance of the business information system, the analysis, audit and warning of the configuration and event, the measurement and assessment of risks and situations, as well as the standardized, routine and normalized operation and maintenance process, so as to ensure the continuous secure operation of the business information system. In addition to the conventional security management function, it provides stronger data analysis performance and richer interactive analysis ability, having become the effective working tool of security analysts.
Construction plan
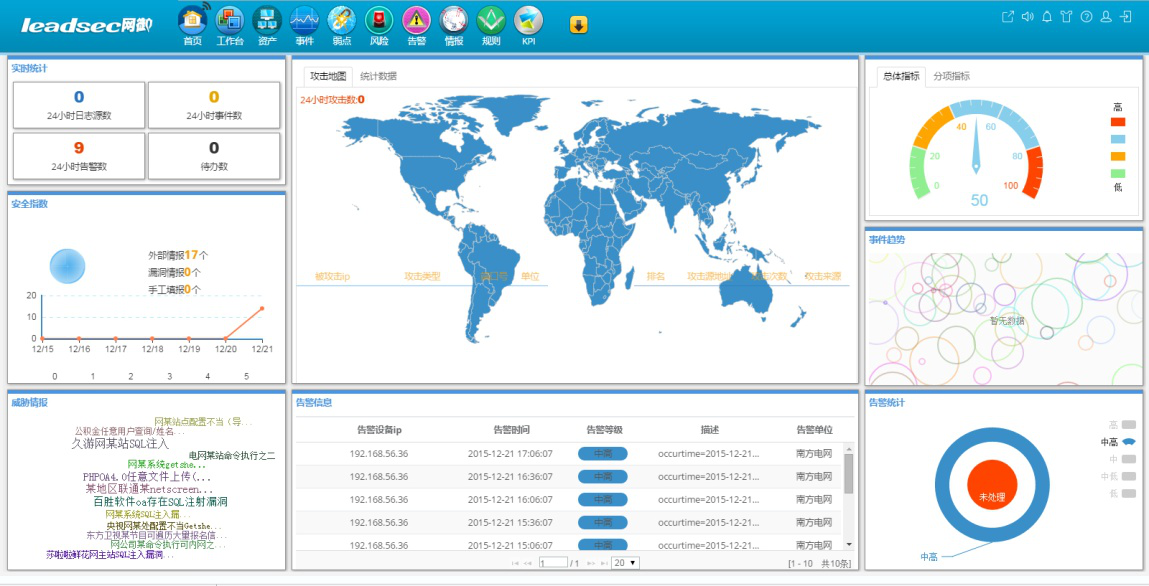
The concept architecture of the Taihe new generation security management platform (SOC) integrating the big data technology is shown in the figure below.
The system consists of the collection layer, big data layer, analysis layer, management and control layer, and presentation layer.
The collection layer collects massive heterogeneous data related to security. Such data is mainly divided into two types, one of which is the high frequency data, known as big data, with the features as massive, high-speed and heterogeneous, mainly including the external stream, operation state and performance data, logs and events, raw traffic mirror image package and stream data, etc., which are collected through high-speed data bus; the other is the low-frequency data, including common asset information, topology information, configuration information, vulnerability information, identity information, vulnerability intelligence and threat intelligence, etc., which are collected through the low-frequency data bus.
The big data layer achieves the pre-processing and storage of the collected data, converts the required data into structured data, indexes and stores the unstructured data, and sends the data to the big data storage system and memory respectively for use by the analysis layer.
The analysis layer achieves real-time and historical analysis of massive pre-processed data, and performs the comprehensive association through various analysis means, including the association analysis, machine learning, operation and maintenance analysis, statistical analysis, OLAP analysis, data mining and malicious code analysis, etc., to complete the data analysis and mining.
The management & control layer achieves the daily security management. The problems found in the analysis layer and the security management platform are presented to the management and control layer, which achieves the information security monitoring and warning, security audit, security measurement, operation management and intelligence management, and intelligence management.
The presentation layer achieves visual presentation of the original data, analysis result data as well as management and control data of massive data, and provides the human-computer interaction interface, presenting the all-round security state to security managers.
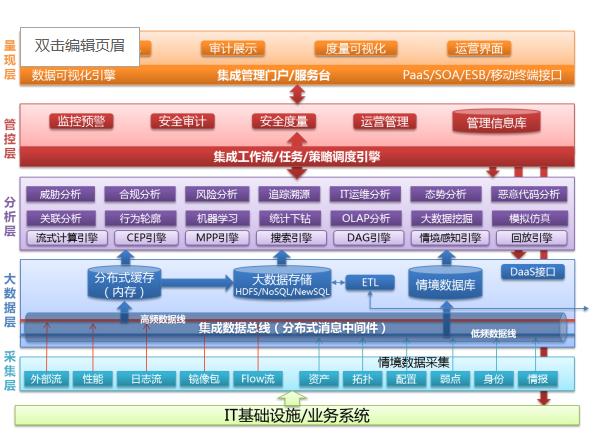
The system functions are generally divided into five parts, namely, Collection, Analysis, Action, Presentation and Supporting.
Information collection: Achieving the collection of asset information, performance information, log and security event information, flow information, configuration security information, vulnerability information, vulnerability intelligence, threat intelligence and other security element information of customer IT resources.
Information analysis: Achieving the performance and availability analysis, configuration compliance analysis, security event analysis, stream behavior security and compliance analysis, vulnerability analysis, risk analysis, security trend analysis and macro situation analysis for all kinds of collected security element information, of which, the risk analysis includes the asset value analysis, vulnerability analysis, threat analysis, risk assessment, impact analysis, etc.; the macro situation analysis includes the address entropy analysis, hotspot analysis, key security indicator analysis, business health analysis, key management indicator analysis; and the security trend analysis includes the attack trend analysis, vulnerability trend analysis and asset security trend analysis.
Security disposal: routine disposal and the exceptional disposal are included. The routine disposal is mainly reflected in the form of work orders of planned tasks; the exception disposal is mainly reflected in the form of response management and warning work order processing. Besides, it also includes the function of security warning management.
User presentation view: The system provides hierarchical user views to the users at different levels and with different roles, which are presented from five management dimensions of monitoring, auditing, risk, operation and trend prediction. The users can also customize the view presentation as needed in their work.
System supporting: the asset management, business management, report management, system management, authority management, cascading management, knowledge management, and global security information bases are included.
Ability to output
Ø Business-oriented unified security management;
Ø All-around monitoring on the performance and availability of the IT system;
Ø Intelligent security event association analysis;
Intelligent stream security analysis;
Indicator-type macro situational awareness;
Integrated security management and control interface.
Professional services
Providing a comprehensive one-stop security operation center solution, with built-in network management, security management and operation and maintenance management functions, and capable of choosing function modules flexibly
The system is simple and practical, with elegant and beautiful interfaces and built-in rich-content instrument panel, and supports skin change, suitable for the management at all levels
Ø Supporting high-speed collection, normalization, association analysis, secure storage and response of logs and events for more than140 domestic and international mainstream devices and systems (continuously updated), and supporting new devices without the need of development
Ø Capable of collecting, analyzing and presenting the performance and availability of various types of mainstream devices and systems (continuously updated), providing the integrated network and security management operation and maintenance capabilities
Ø Having the most perfect security management knowledge base in China, including the security event base, security policy base, warning information base, vulnerability base, association rules base, processing plan base, case base, etc
Ø Having the most leading security event association analysis and situation awareness capabilities in China, and can realize the quantitative analysis and security situation assessment of the security risks across the network, and having the situation prediction capability
Ø It is the first domestic security management platform that adopts the big data analysis architecture. The platform realizes the horizontal elastic expansion of computing capacity and protects the existing investment of customers by adopting the mainstream big data analysis architecture and technology and making full use of parallel distributed information collection, computing and storage technologies
Ø The system is designed with the open and flexible platform architecture, which can be scaled, tailored, extended and integrated
Ø Powerful customization ability, supported by a most professional customized development team and an operation and maintenance implementation team
The big data version of the Leadsec security management system is widely used in the government, E-government extranet, finance, telecommunications, power, media as well as large and medium-sized enterprises, meeting customer demands for information system classified protection as well as internal security management and analysis of enterprises.

Service hotline:
400-810-7766 (24H)
E-mail:
shfw@leadsec.com.cn
Address:
Zhongguancun, 8 dongbeiwang west road, haidian district, BeijingSoftware park 21